6 Steps to a Penetration Test
Getting a penetration test can seem overwhelming, but following these steps can help ensure that your penetration test goes as smoothly as possible.
Getting a penetration test can seem overwhelming, but following these steps can help ensure that your penetration test goes as smoothly as possible.

A penetration test, or pen test, is a security assessment that simulates an attack by a malicious party on a network or application to identify security flaws. This test is coordinated ahead of time and executed with an attempt to avoid damaging any system.
At the end of the test, your pentesting firm will provide you with a report that includes found issues and weaknesses along with suggestions for how to remediate them.
See also: How Much Does a Pentest Cost?
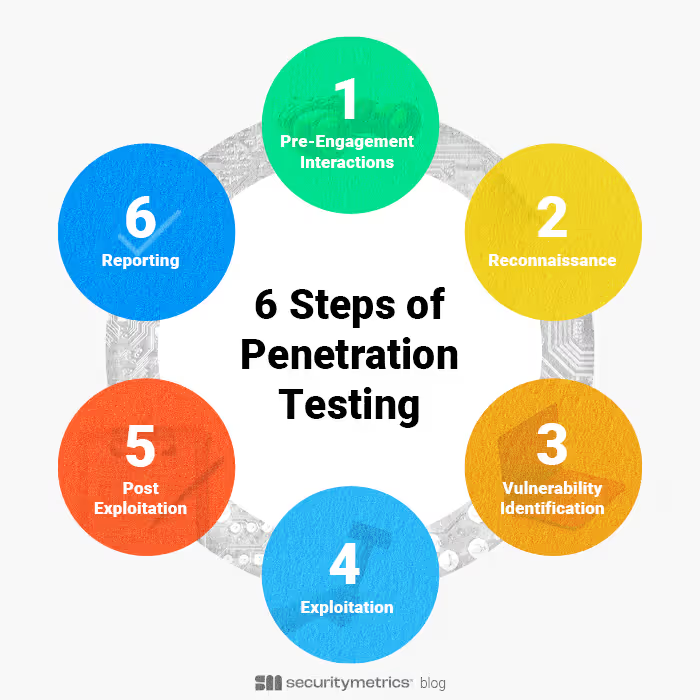

During this phase the tester collects extensive information about the target system, including network topology, operating systems, applications, user accounts, and other pertinent details. This data helps the pen tester determine how to test the system. The pentester uses the attack surface, customer concerns about security, and previous breach history to define objectives for the engagement and the scope of the engagement
Scoping is a crucial component of an effective penetration test. Even though scoping is one of the most important components to a successful penetration test, it is often overlooked.
Scoping is determining what systems are covered or need to be assessed or included as part of your penetration test. It includes identifying systems that store, process, or transmit data that could impact security and the systems connected to them.
Scoping also considers how data enters and exits the organization.

The initial phase of penetration testing is reconnaissance. During this phase, a pentester prioritizes where to spend their time based on what they discovered during the pre-engagement interactions, customer objectives, previous security history (e.g. breaches), and active attacks that are happening in the wild.
Scanning is also part of reconnaissance. Testers utilize various tools to identify open ports and assess network traffic on the target system. This helps pen testers uncover potential entry points for attackers. While vulnerability scanning can be performed separately as an automated process, it falls short of a comprehensive penetration test that can determine the actual level of access hackers may gain.

Essentially, the vulnerability identification phase of penetration testing is the discovery of vulnerabilities. Testers leverage the data gathered from reconnaissance to identify potential vulnerabilities and evaluate their exploitability. While vulnerability assessment is valuable as a standalone tool, it becomes even more potent when integrated with other phases of penetration testing.
To determine the risk associated with identified vulnerabilities, penetration testers can rely on various resources, including the National Vulnerability Database (NVD). The NVD, maintained by the U.S. government, analyzes software vulnerabilities published in the Common Vulnerabilities and Exposures (CVE) database. It assesses the severity of known vulnerabilities using the Common Vulnerability Scoring System (CVSS).

After vulnerabilities have been discovered, the exploitation phase of penetration testing begins. During this stage, the penetration tester uses the vulnerabilities that are discovered in the previous stages to perform a malicious action (e.g. get privileged access) and exploit the identified vulnerabilities. While conducting these simulated attacks, testers must exercise caution to avoid compromising or causing damage to the system.

This phase is designed to help the tester “identify and document sensitive data, identify configuration settings, communication channels, and relationships with other network devices that can be used to gain further access to the network, and set up one or more methods of accessing the [system] at a later time” (PTES).

After the exploitation phase, the penetration tester creates a comprehensive report summarizing the findings of the penetration test. This final phase of penetration testing involves documenting vulnerabilities and offering remediation suggestions to enhance the organization's security posture.
A well-constructed penetration testing report includes essential sections such as a thorough inventory of identified vulnerabilities (including CVSS scores), an assessment of their impact on the business, an explanation of the level of difficulty encountered during the exploitation phase, a technical risk briefing, remediation guidance, and strategic recommendations.
These components help organizations understand their security risks and take appropriate measures to address them effectively.
The following steps will enable you to understand what your attack surface is and prioritize the scope of an engagement. Both of these will be crucial in communicating with a point of contact when defining the scope of a penetration test.
Often the effectiveness of an engagement will be determined by your ability to communicate what your attack surface is and what you are most concerned about.
The following steps will help you develop an asset inventory and prioritize your scope.
An accurate and up-to-date network diagram acts as a blueprint, providing a visual representation of your organization's network infrastructure and enabling penetration testers to understand your network architecture for more focused and efficient testing.
Data flow maps complement network diagrams by illustrating the flow of sensitive information within an organization's systems, aiding penetration testers in identifying vulnerabilities and weak points in data handling processes for a comprehensive security assessment.
Maintaining an up-to-date list of active ports and services facilitates efficient penetration testing by providing testers with crucial information about accessible services, enabling them to identify potential issues more effectively and ensuring a smoother testing process.
Having the knowledge from your network diagram and data flow map readily available, even if not all of it needs to be shared, enhances collaboration and efficiency during the penetration testing process, allowing for quick resolution of unexpected issues and demonstrating a commitment to a comprehensive assessment.
After completing your penetration test and remediation, you can focus on improving future testing experiences and preventing future vulnerabilities.
Implement process and policy changes based on the lessons learned from the test and integrate them into your standard practices. Provide additional training to developers and network engineers to enhance their skills and resources. Stay vigilant about software updates and regularly perform application/port scanning to maintain security.
It's recommended to plan your testing schedule with a time cushion, especially if compliance requirements are involved.
When choosing a penetration testing firm, look for a partner that prioritizes collaboration and open communication. Ensure that both parties are comfortable giving and receiving feedback to improve processes.
At SecurityMetrics, we communicate through a pen test coordinator. It’s a great way for clients to interact with the pentest team more often. We find that utilizing a human project management interface makes the entire process simpler, faster, and a better experience for all parties.
Prepare adequately for the test to ensure smooth execution, and view the testing firm as a partner focused on improving your company's security. Keep in mind that remediation may take longer than expected, so plan accordingly for future test cycles.
Whether your business needs a penetration test for an industry compliance requirement, or because of a security incident, the process can seem overwhelming. However, our 20+ years of experience have helped us develop processes to make your compliance as thorough and painless as possible so that you can keep your organization secure.